Chinese Nation-State Threat Actor Targets Japanese Organizations with Stealthy Malware Campaign
Japanese organizations are currently being targeted by a Chinese nation-state threat actor employing sophisticated malware families, such as LODEINFO and NOOPDOOR. These tools are used to harvest sensitive information from compromised hosts, often remaining undetected for periods ranging from two to three years. The Israeli cybersecurity company Cybereason has been tracking this campaign under the name “Cuckoo Spear,” attributing it to a known intrusion set known as APT10. This group is also referred to by various names, including Bronze Riverside, ChessMaster, Cicada, Cloudhopper, MenuPass, MirrorFace, Purple Typhoon (formerly Potassium), and Stone Panda.
Malware Utilization and Data Exfiltration
According to Cybereason, the actors behind NOOPDOOR not only utilized LODEINFO during the campaign but also leveraged the new backdoor to exfiltrate data from compromised enterprise networks. The malware deployment is part of a broader strategy to infiltrate and extract valuable information while avoiding detection.
The findings from Cybereason come shortly after a warning from JPCERT/CC, which highlighted cyber attacks by the threat actor targeting Japanese entities using the two malware strains. Earlier in January, ITOCHU Cyber & Intelligence revealed an updated version of the LODEINFO backdoor that incorporates anti-analysis techniques, emphasizing the use of spear-phishing emails to propagate the malware.
APT10’s Structure and Tactics
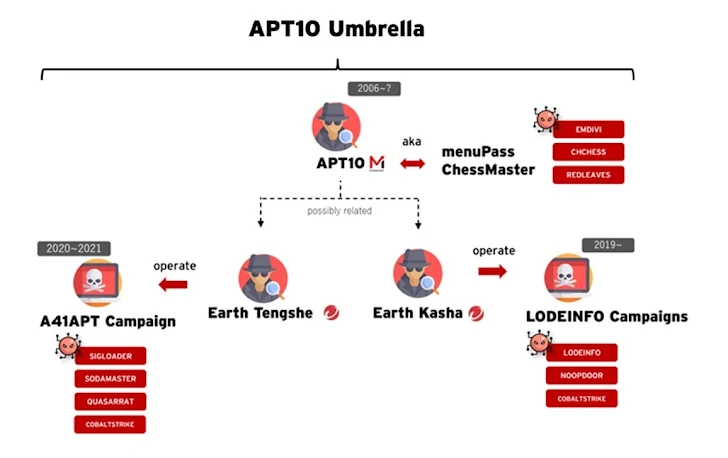
Trend Micro, which originally coined the term “MenuPass” to describe the threat actor, has characterized APT10 as an umbrella group comprising two clusters: Earth Tengshe and Earth Kasha. This hacking crew has been operational since at least 2006. Earth Tengshe is associated with campaigns distributing SigLoader and SodaMaster, while Earth Kasha exclusively uses LODEINFO and NOOPDOOR. Both sub-groups have been observed targeting public-facing applications to exfiltrate data and information from networks.
Connections and Evolution
Earth Tengshe is also linked to another cluster codenamed Bronze Starlight (also known as Emperor Dragonfly or Storm-0401), which has a history of operating short-lived ransomware families such as LockFile, Atom Silo, Rook, Night Sky, Pandora, and Cheerscrypt. Conversely, Earth Kasha has recently shifted its initial access methods by exploiting public-facing applications since April 2023. This shift includes taking advantage of unpatched flaws in Array AG (CVE-2023-28461), Fortinet (CVE-2023-27997), and Proself (CVE-2023-45727) instances to distribute LODEINFO and NOOPDOOR (also known as HiddenFace).
Capabilities of LODEINFO and NOOPDOOR
LODEINFO is a versatile backdoor equipped with various commands to execute arbitrary shellcode, log keystrokes, take screenshots, terminate processes, and exfiltrate files to an actor-controlled server. NOOPDOOR, sharing code similarities with another APT10 backdoor known as ANEL Loader, features functionalities to upload and download files, execute shellcode, and run additional programs.
Persistence and Long-Term Infiltration
Cybereason noted that LODEINFO appears to be used as a primary backdoor while NOOPDOOR serves as a secondary backdoor, maintaining persistence within the compromised corporate network for more than two years. The threat actors achieve this persistence by abusing scheduled tasks, ensuring they remain entrenched in the targeted environments for extended periods.



